To start you off, we reveal the codes for two or three lettersEnigma decoder Decrypt and translate enigma online The Enigma cipher machine is well known for the vital role it played during WWII Alan Turing and his attempts to crack the Enigma machine code changed history Nevertheless, many messages could not be decrypted until today Bitwise calculator Text to base64ENIGMA Chapter 1 – Historical Background ENIGMA Chapter 2 – The Invention of the Enigma Machine The Enigma machine is a polyalphabetic substitution cipher machineThis post will provide a little background information on the differences between monoalphabetic and polyalphabetic substitution ciphers and on the specific characteristics of cipher alphabets created by an Enigma
Enigma The German Cipher Machine
Easy alphabet enigma code
Easy alphabet enigma code-Acknowledgements) Retraced some links— Website history External Video Universal Enigma in action, and a basic tutorial here (courtesy of poughkeepsieblue) — Dec 13 The three rotors in the Enigma machineSourceWikipedia The military Enigma Machine had another set of encryption layers by using switchboards where each alphabet got mapped to another alphabet




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium
CryptiiText to Enigma Cryptiiv2 Cryptii Convert, encode, encrypt, decode and decrypt your content online Attention! The Enigma machine is a complicated apparatus consisting of a keyboard, a set of rotors, an alphabet ring, and plug connections, all configurable by the operator For the message to be both encrypted and decrypted, both operators had to know two sets of codes A daily base code, changed every 24 hours, was published monthly by the Germans The encryption code returns an element from the alphabet array {const position = alphabet indexOf (char toUpperCase ());
Incandescent Alphabets is a remarkable look at the intersections between language and psychosis Rogers extends our understanding of madness beyond the biomedical model, and delivers a view of psychosis that is rooted in a deep respect for the human spirit and each individual's experienceEnigma Permutations, Encryption Decryption Keys, Code, Software We are sampling here Enigma code by generating all permutations, then selecting permutations that do not repeat absolutely any element in the same position This article follows an analysis of Enigma and Venoma coding and the 14 Imitation Game film inspired by the reallife The enigma machine was used in World War II to encrypt secret messages The Enigma machines are a series of electromechanical rotor cipher machines The first machines were invented at the end of World War I by German engineer Arthur Scherbius and were mainly used to protect commercial, diplomatic and military communication Enigma machines became
Enigma Enigma was a ciphering (code communication) system used by the German military from 1926 until the end of World War II, and by several other nations for some years after Enigma was the first mechanized messageencryption system to see wide use Enigma produced such thoroughly scrambled messages that for many years its cipher was The mathematical prowess of the Polish Cypher Bureau had secretly first broken Enigma codes in 1932, with the aid of French intelligence At the eve of the war they handed their work to the AlliesThe Enigma rotor cipher machine was potentially an excellent system It generated a polyalphabetic substitution cipher, with a period before repetition of the substitution alphabet that was much longer than any message, or set of messages, sent with the same key A major weakness of the system, however, was that no letter could be enciphered to itself



Enigma Procedure



Http Www Singingbanana Com Enigmaproject Maths Pdf
C = 2) Shifting up the alphabet means, an A becomes a B, a B a C, and so onThis is somewhat simpler than the real Enigma machines that used three or four rotors which could be rearranged and selected from a selection, and generally featured a plugboard as well However, we do use an alphabet with n=72 instead of n=26, soEnigma 00 updates the Enigma algorithm for the twentyfirst century Like the original Enigma, E2K is a polyalphabetic cipher each plaintext letter is mapped to a ciphertext letter by means of a permuted alphabet Unlike the original Enigma, the permuted alphabet at each plaintext position is not determined by a series of rotors




Code And Ciphers Julius Caesar The Enigma And The Internet



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
I am working is a project that would implement a cipher that would output ciphertext that would be easy to transmit through morse code, just like they did in the days of Enigma This code simulates the Enigma machine, minus the plugboard Here's some test code that illustrates how the machine's construction and use >>> r1 = Rotor ("VEADTQRWUFZNLHYPXOGKJIMCSB", 1) >>> r2 = Rotor ("WNYPVJXTOAMQIZKSRFUHGCEDBL", 2) >>> r3 = Rotor ("DJYPKQNOZLMGIHFETRVCBXSWAU", 3) >>> reflector = Reflector How does Enigma code work?




Pocket Enigma Cipher Machine Educational Toy Which Demonstrates Some Of The Underlying Principles Of The Enigma Machine From Enigma Machine Enigma Bletchley




Cipher Cracking When Computer Bugs Were Real And Bits Were Cogs
Enigma's Secrets How it Worked and How the Code was Broken By way of introduction, see the Historical Background to Enigma and the Key Players Involved The Working Principle The Enigma machine basically provided a simple substitution of a plaintext symbol with a different ciphertext symbol generated by the machine What made the machine special however was that The code crackers were helped when German signal operators got lazy, repeating easytofind patterns, like Heil, Hitler, "wetter" for weather or a girlfriend's name During World War II, the Germans used the Enigma machine to develop nearly unbreakable codes for sending messages Credit Greg Goebel The Enigma had three rotors, connected in series They were thick discs, each with 26 input points (one for each letter of the alphabet) and as many output points




Amazon Com Enigma 37 Encryption Machine Able To Encode Both Letters And Numbers Handmade



Enigma Procedure
Onto itself The alphabet consists solely of the 26 letters in one case (there were various conventions for spaces and punctuation) Plain substitution ciphers are easy to break (you've probably seen puzzles in newspapers that consist of breaking such ciphers) The Enigma, however, implements a progressive substi 25 June 21 Codewords are like crossword puzzles but have no clues!Instead, every letter of the alphabet has been replaced by a number, the same number representing the same letter throughout the puzzle All you have to do is decide which letter is represented by which number!




Vegetarian Pig Lover A History Of Codes And Ciphers In Code And Cipher




Picture Ciphers And Codes Coding Alphabet Code
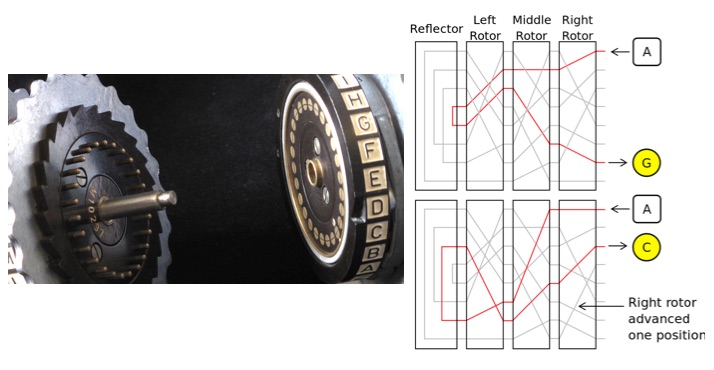
NATO Phonetic Alphabet The NATO phonetic alphabet is a Spelling Alphabet, a set of words used instead of letters in oral communication (ie over the phone or military radio) Each word ("code word") stands for its initial lette r (alphabetical "symbol") The 26 code words in the NATO phonetic alphabet are assigned to the 26 letters of the 28position wheels, Swedish alphabet, trivial ringsetting Changelog Website Minor text updates regarding UE v26 (Features;Assuming that the offset is correct, the Enigma machine encodes the plaintext N into B at index 3 At index 5, the machine turns B into P At index 9, the letter N becomes a P Given the symmetry of the Enigma machine, however, you know that typing a P at index 9 would have produced an N, which is the letter that began this chain back at offset 3




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium



Enigma Codeproject
An enigma style simulation machine in Python 3 This code made a few breaks back in my spare time There are, however, a few alterations to the original machine that this simulation shows, one being the alphabet, another being the amount of rotors If you happen to run this you'd find this to be slow (please run in console, not shell)This meant that the same letter of the alphabet would be encoded to a different letter each time it was used in a message (If this weren't the case it would have been almost trivial to crack an Enigma message) Effectively each letter in a message was encoded using its own unique code It was this fact that made the Enigma so difficult to defeat The need to conceal the meaning of important messages has existed for thousands of years Over time, people have found increasingly complex ways of encoding their messages as the simpler ways are decoded with greater ease Contrary to laymanspeak, codes and ciphers are not synonymous A code is where each word in a message is replaced with a code word or



Q Tbn And9gcrxgl2jcejwxmxpleltb3nrau65i0fzbz0gcfwvhfno6hrypsma Usqp Cau




Cxncjoa77wzf6m
The enigma keyboard The user interface is very simple — it is represented by a keyboard of 26 letters It is used to insert the input in the machineColor code use different colored shapes to create your own cipher There's 7 colors so all you need is to choose 6 different shapes and you've got the whole alphabet and numbers covered Keyboard code since computer keyboards are all the same they can be used as the key to make a ridiculously challenging code for your escape game Just grabSimplified Enigma machine that is limited to a six letter alphabet Figure 4 Simplified version of a Enigma machine with one rotor The disk on the left is the keyboard, the middle ring is the rotor, and the disk on the right is the lampboard The wiring of the rotor determines how the plaintext letters will be encrypted



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf
The Enigma machine Encrypt and decrypt online The Enigma cipher machine is well known for the vital role it played during WWII Alan Turing and his attempts to crack the Enigma machine code changed history Nevertheless, many messages could not be decrypted until today Caesar cipher Crockford's Base32 Vigenère cipher The Enigma 'typewriter' In 01, the release of the feature film Enigma sparked great interest in the tweedy world of the boffins who broke Nazi Germany's secret wartime communications codes ButEnigma has an electromechanical rotor mechanism that scrambles the 26 letters of the alphabet In typical use, one person enters text on the Enigma's keyboard and another person writes down which of 26 lights above the keyboard lights up at each key press READ Should exams be banned?




The Enigma Cipher Machine And Breaking The Enigma Code




The Enigma Cipher Machine And Breaking The Enigma Code
This version of cryptii is no longer under active development Find the latest version on cryptiicom Cryptii is an OpenSource web application under the MIT license where you can encode and decode between different formatSolve our Enigma code by correctly allocating each letter to its corresponding number All letters of the alphabet are used The Enigma code is set in a crossword format, each row or column will spell a word when completed correctly We have given you a starting either a letter or letters The Enigma machine would automatically convert each letter into a different letter of the alphabet, through a process of random substitution The encrypted text would be sent to another operator whose deciphering machine was similar and compatible with the first operator's machine only in this case the second Enigma machine would convert the



Q How Good Is The Enigma Code System Compared To Today S Publicly Available Cryptography Systems Ask A Mathematician Ask A Physicist



1
For thousands of years, ciphers have been used to hide those secrets from prying eyes in a catandmouse game of codemakers versus codebreakers These are some of history's most famous codes 1 Enigma, device used by the German military to encode strategic messages before and during World War II The Enigma code was first broken by the Poles in the early 1930s In 1939 the Poles turned their information over to the British, who set up the codebreaking group Ultra, under mathematician Alan M Turing The Enigma code machine ( image source ) Enigma machines also used a form of substitution encryption Substitution encryption is a simple way to decipher messages, but these codes are very easy to crack The Caesar cipher is a good example of a substitution encryption scheme The Caesar cipher transfers several positions for each letter of the



Substitution Cipher Wikipedia




Code Breaking Instrumental In Ending World War Ii American Association For The Advancement Of Science
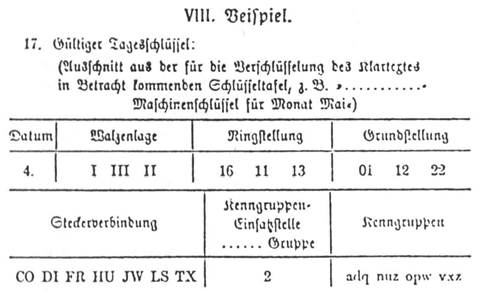
60 \times \times 150,738,274,937,250 = 158,962,555,217,6,360,000 60××150,738,274,937,250 = 158,962,555,217,6,360,000 total number of ways to set a militarygrade Enigma machine 7 Physicist Freaking terrible The Enigma machine used a "rolling substitution cypher" which means that it was essentially a (much more) complicated version of "A=1, B=2, C=3, " The problem with substitution cyphers is that if parts of several messages are the same then you can compare their similarities to break the code The next step is to shift all the letters up the alphabet by one for each letter that we go up in the alphabet So, if we want ring setting C, we go up by 2 in the alphabet (Start out at A, B = 1;
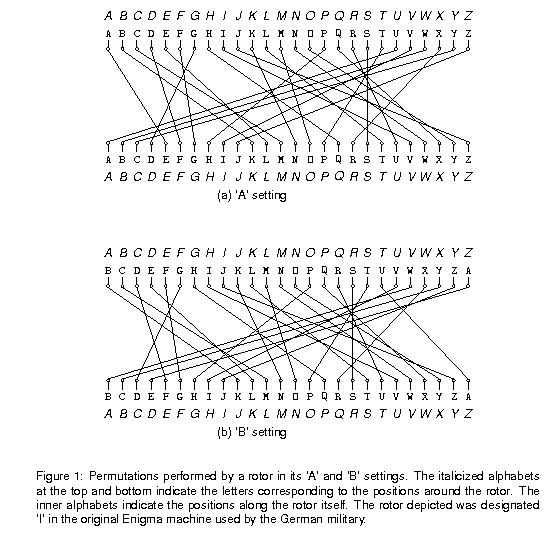



Project 1 Cs 61b Fall 16




Team Name Team 13 Programmer B Tester
The Principle of the Enigma Tony Sale's Codes and Ciphers one for each letter of the alphabet, connecting a battery to the top letter terminal where the key is pressed Continue to the next page to see how the Enigma was put together and how it was given a further layer of complexity for German military use This page was created byA code is a system of symbols, letters, words, or signals that are used instead of ordinary words and numbers to send messages or store information A code is used to keep the message short or to keep it secret Codes and ciphers are forms of secret communication The Germans began using the Enigma machine in the late 19s By late 1932, the Poles had broken the Enigma code In 1939 just a matter of weeks before Hitler invaded Poland, the Polish Cipher Bureau shared its technology with the French and the British, who continued to decode messages



The Enigma Machine And The Ultra Secret South African Military History Society




Enigma 2 World War Who Hacked The Enigma Code And When Who Could Decipher The Enigma Code
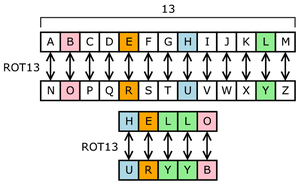
Have your child follow these easy steps to use the Caesar Cipher Step 1 Write out the entire alphabet in a line Step 2 Choose a number to be your "rotation" amount In this example, it is 7 Count this many letters into the alphabet Step 3 Under your first line, starting at the letter you "rotated" to, rewrite the alphabet



Github Mustachelab Php Enigma The Enigma Wrote In Php Cipher Machine Was Invented By A German Engineer Arthur Scherbius Who Applied For His Patent On February 23 1918 This Was In The Same




Enigma Machine Simple English Wikipedia The Free Encyclopedia




The Human Errors That Defeated Enigma Openmind




Enigma Cipher Machine
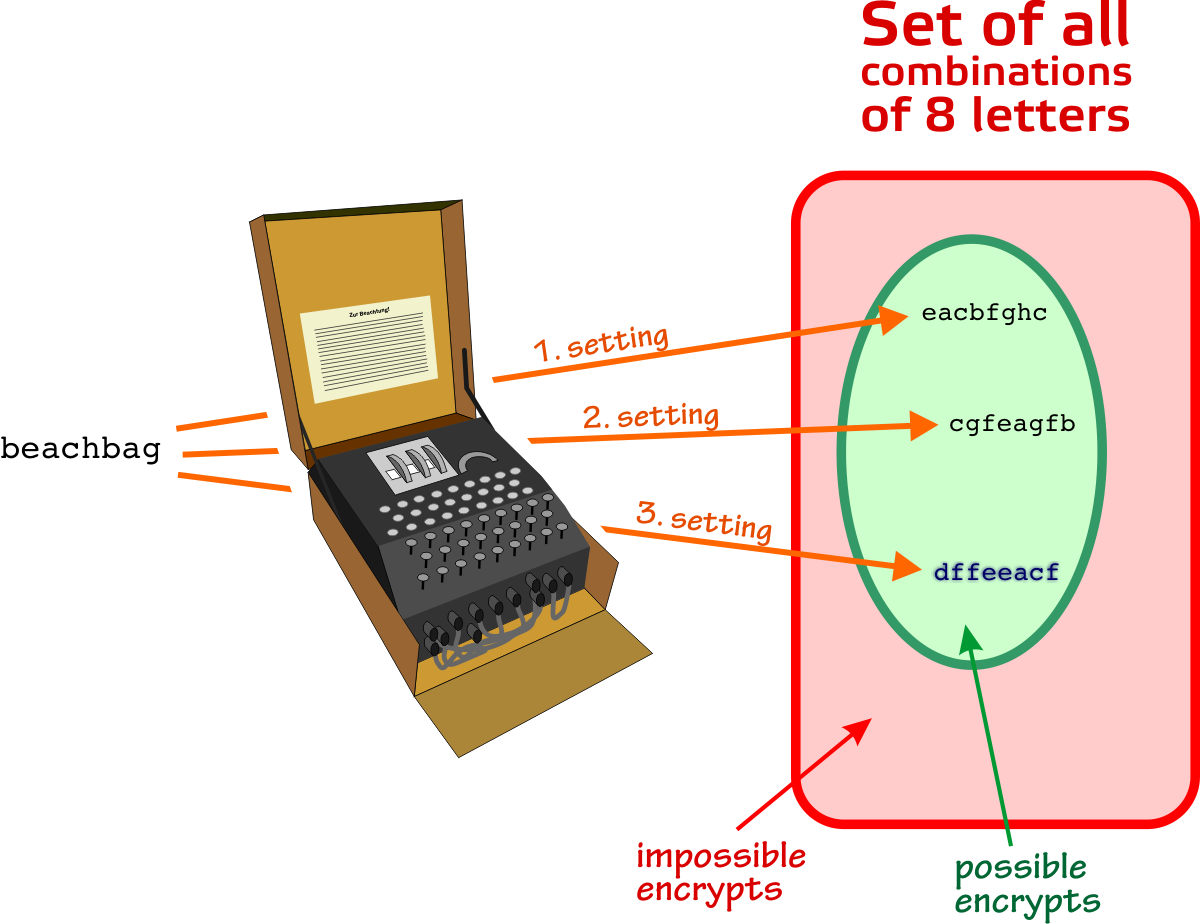



Enigma The German Cipher Machine




Caesar Ciphers



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher




How To Crack The Enigma Code Calculate




How To Build An Enigma Machine Virtualisation In Python By Vasile Păpăluță Analytics Vidhya Medium
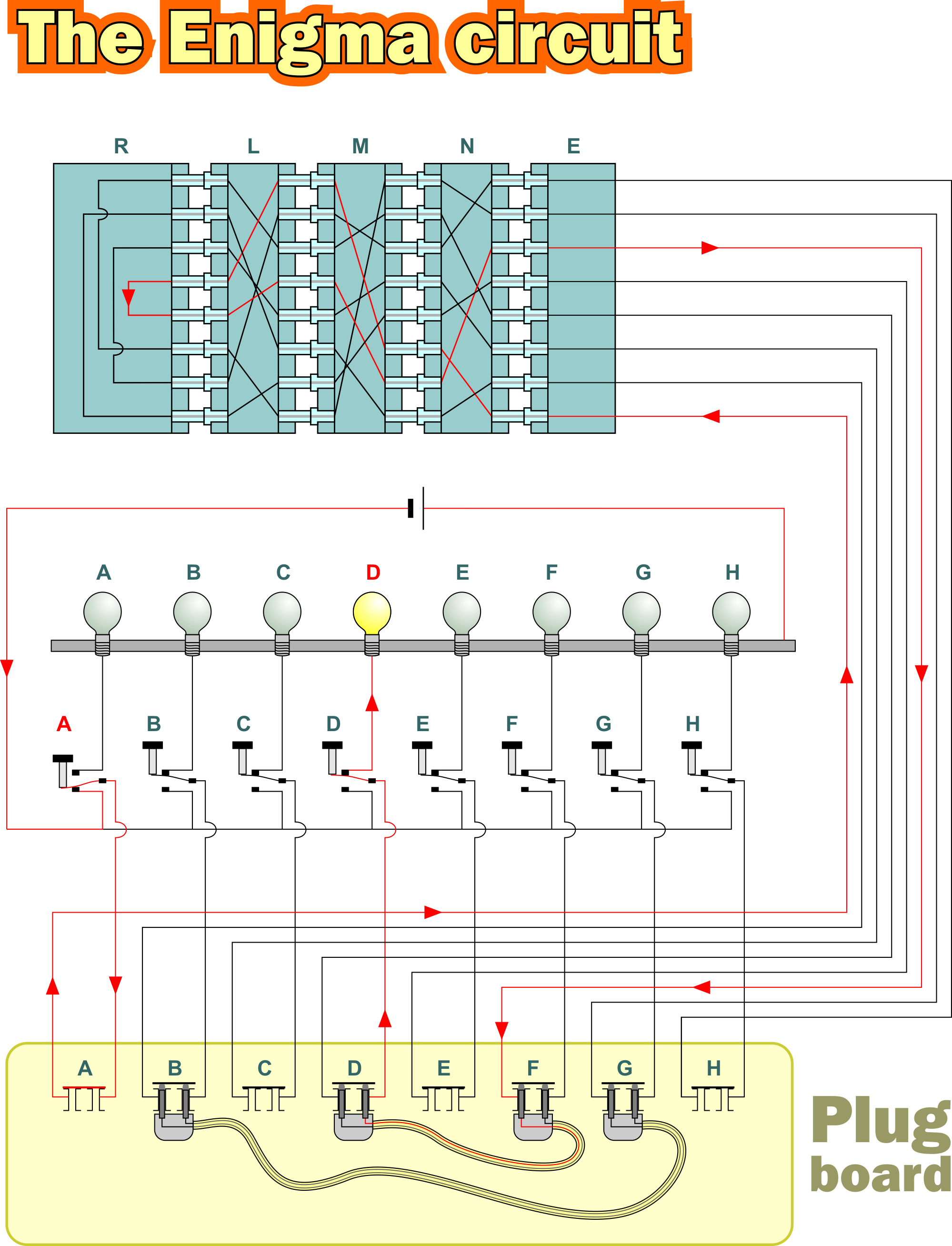



Enigma The German Cipher Machine




The Enigma 1
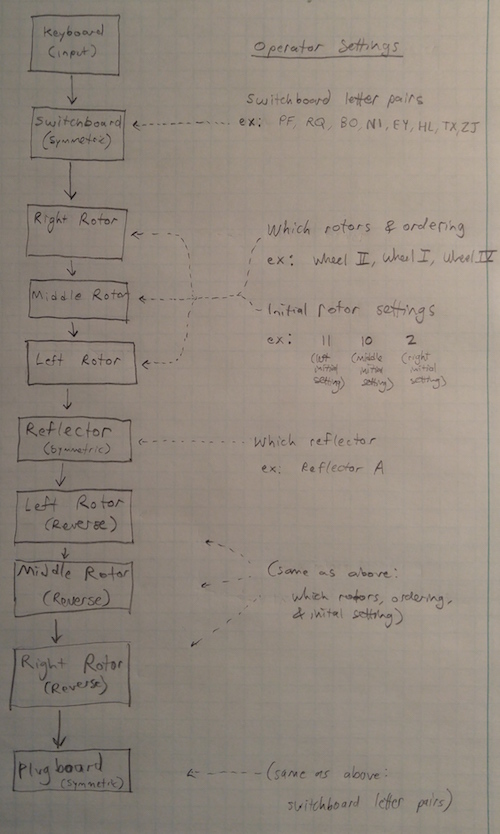



Charlesreid1



1




Cipher Machines Columbus State University



What Actually Was The German Enigma Machine What Was The Code That Needed To Be Cracked And What Messages Did They Actually Send Quora
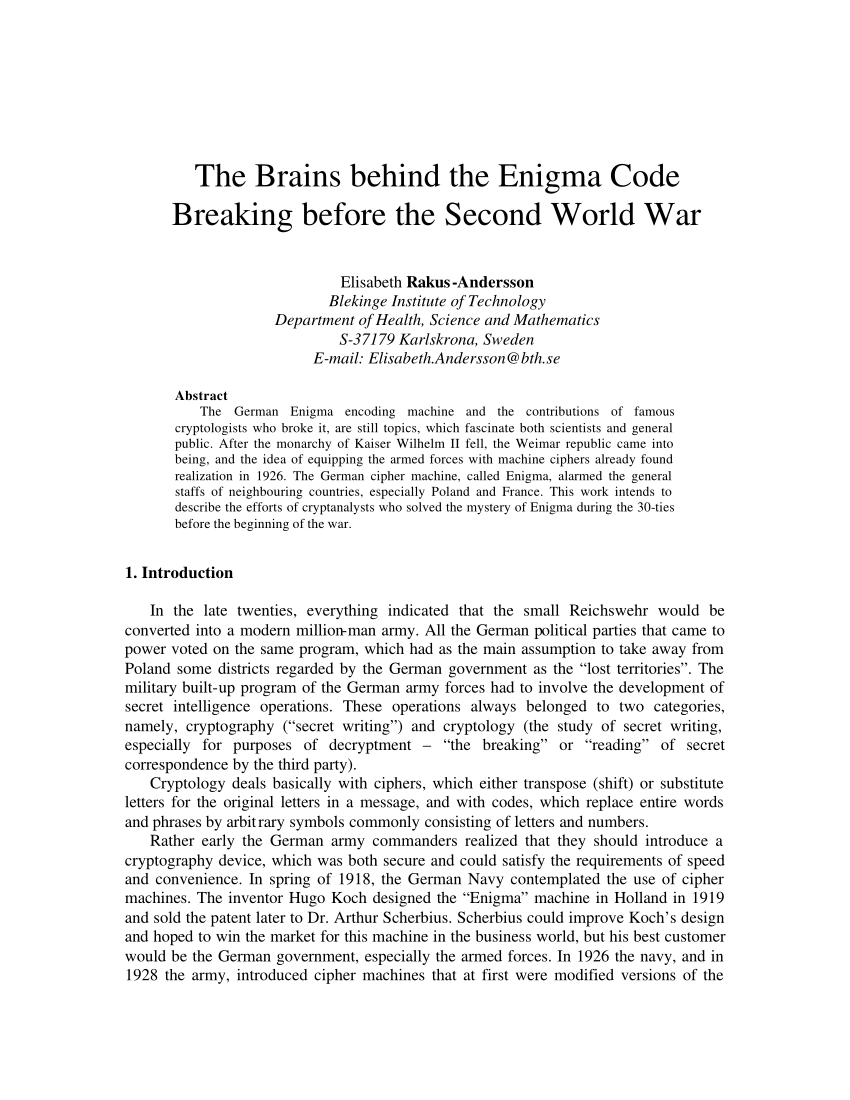



Pdf The Polish Brains Behind The Breaking Of The Enigma Code Before And During The Second World War



Enigma And A Way To Its Decryption




The Enigma Enigma How The Enigma Machine Worked Hackaday



Understanding The Enigma Swimming The Styx




Charlesreid1




Enigma Code Breaking Machine Rebuilt At Cambridge News8plus Realtime Updates On Breaking News Headlines



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf




The Enigma Cipher Machine And Breaking The Enigma Code




Enigma Codeproject




1 2 3 Code Cycle 3 Activities Lesson 3 4 How To Ensure A Message Is Secure Le Site De La Fondation La Main A La Pate



Enigma Details




Enigma Cipher Machine




Ukw D



Enigma Machine Kata
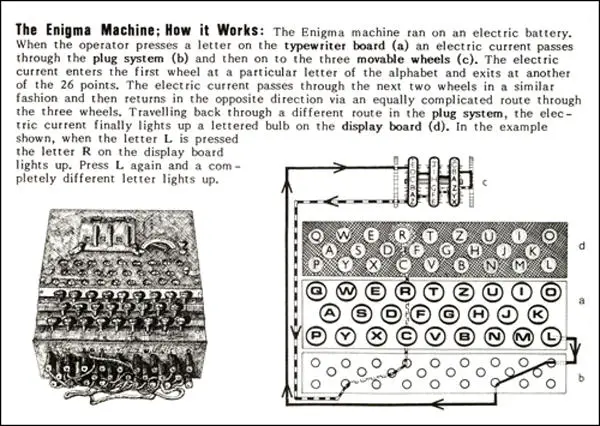



Enigma Machine
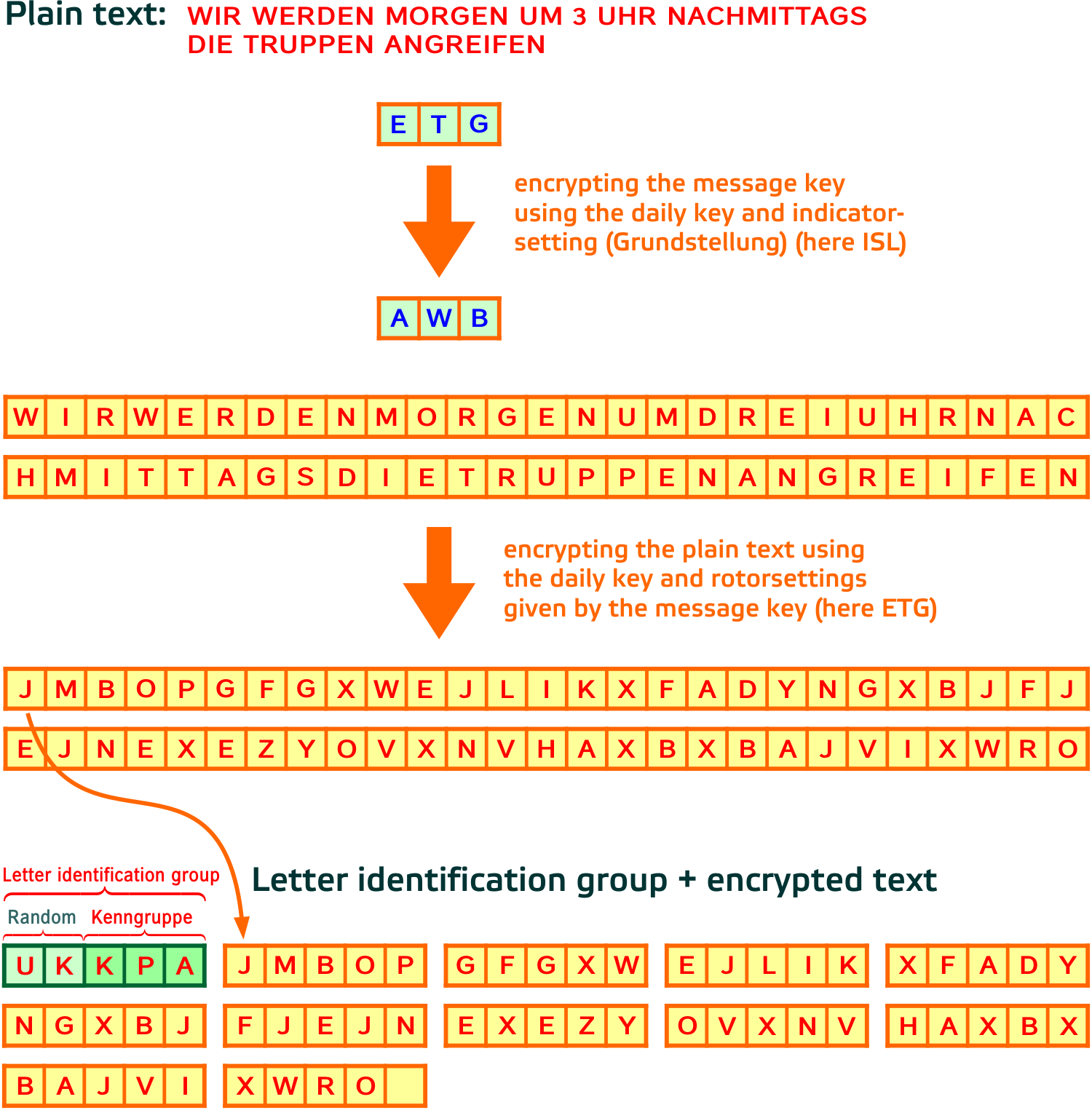



Enigma The German Cipher Machine



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher




11 Cryptographic Methods That Marked History From The Caesar Cipher To Enigma Code And Beyond




Cryptanalysis Of The Enigma Wikipedia




Enigma The German Cipher Machine




Team Name Team 13 Programmer B Tester




Cipher Machines
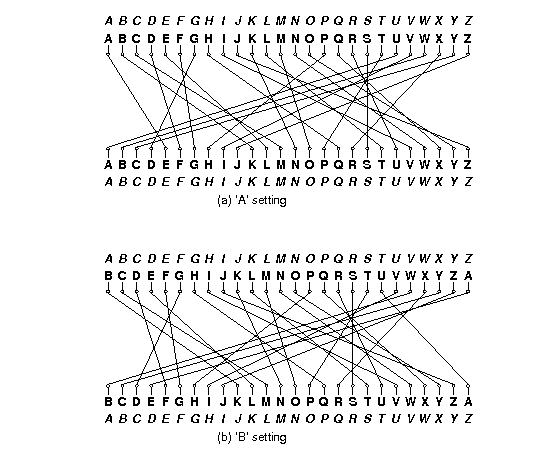



Project 1 Cs 61b Spring




Build Your Own Enigma Cipher Machine Ieee Spectrum



Enigma Procedure




Polyalphabetic Substitution Cipher As Used By Enigma Machines Vigenere Cipher Ciphers And Codes Coding
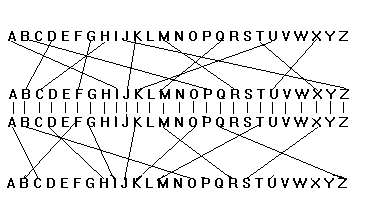



The Enigma 1




Cxncjoa77wzf6m




Pdf The Polish Brains Behind The Breaking Of The Enigma Code Before And During The Second World War




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium




10 Codes And Ciphers Listverse Alphabet Code Ciphers And Codes Coding
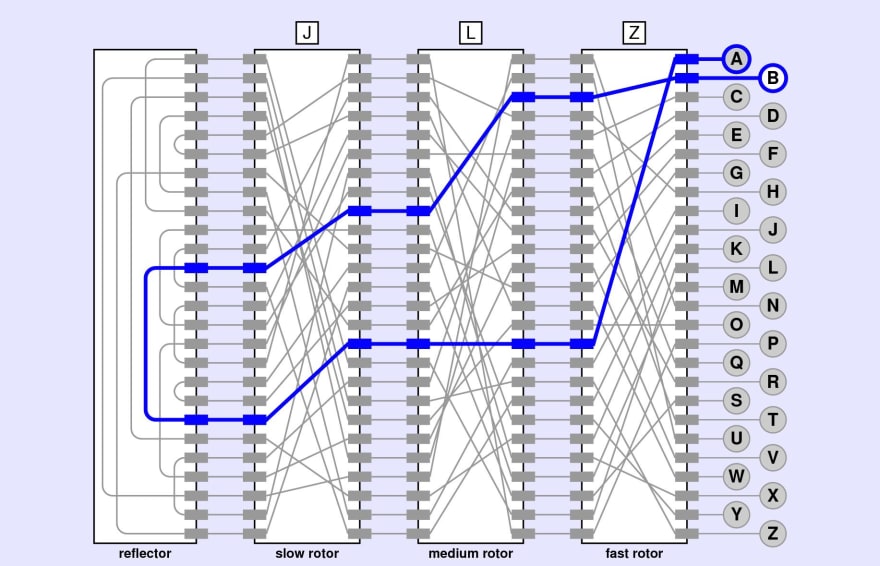



Enigma Machine How Does The Famous Encryption Device Work Dev Community



How Does The Enigma Machine S Reflector Work Quora
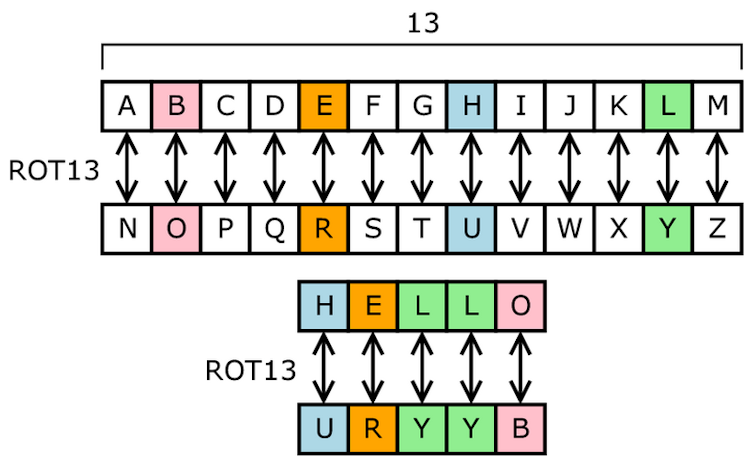



Codebreaking Has Moved On Since Turing S Day With Dangerous Implications



The Enigma A Look At The Ww2 German Cypher Machine A Ab
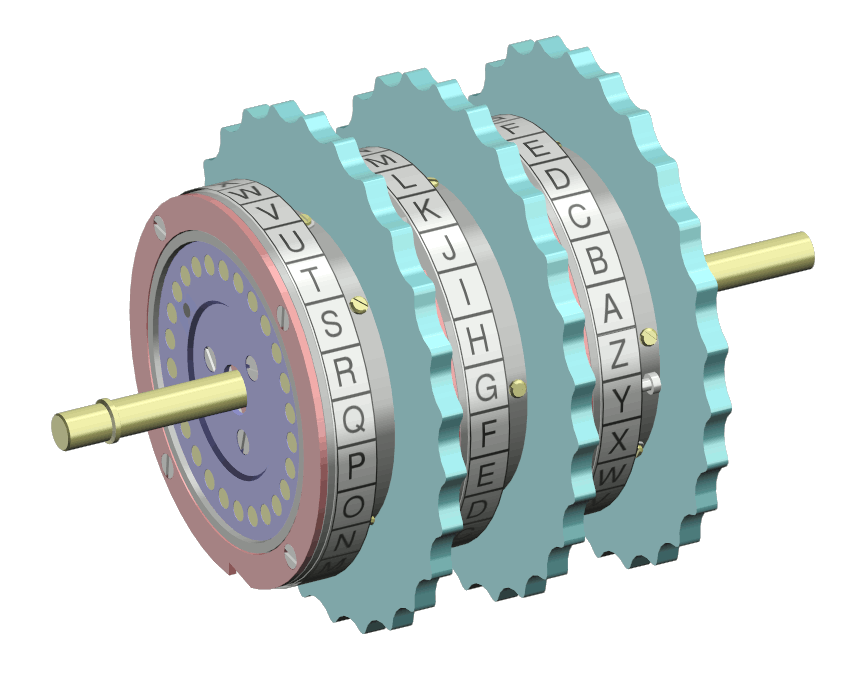



Cryptanalysis Of The Enigma Wikipedia



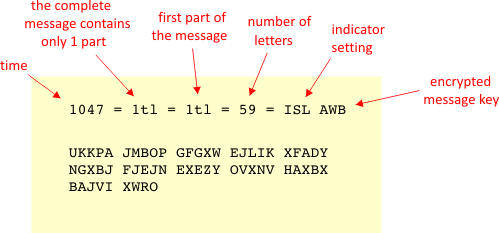
Cryptology I Vigenere Based Systems



How Did The Wwii Enigma Machine Work And How Did They Break It Quora



The Enigma Machine And The Ultra Secret South African Military History Society




Enigma 37 Encryption Machine With Letters Numbers



Cryptography Cryptography



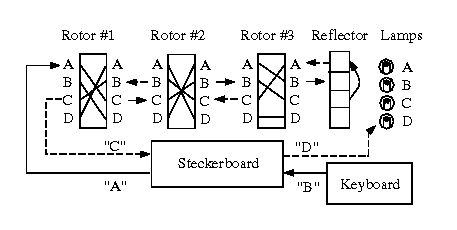
Enigma The German Cipher Machine




The Human Errors That Defeated Enigma Code Lab




A1 Enigma



5 0 The Mechanization Of Ciphers




Rotor Machine Wikiwand




Project 1 Enigma




The Enigma Cipher Machine And Breaking The Enigma Code




1 2 3 Code Cycle 3 Activities Lesson 3 4 How To Ensure A Message Is Secure Le Site De La Fondation La Main A La Pate
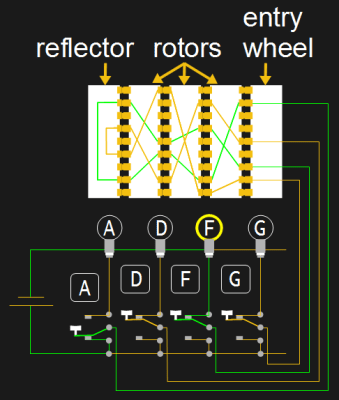



The Enigma Enigma How The Enigma Machine Worked Hackaday




Enigma Machine Brilliant Math Science Wiki
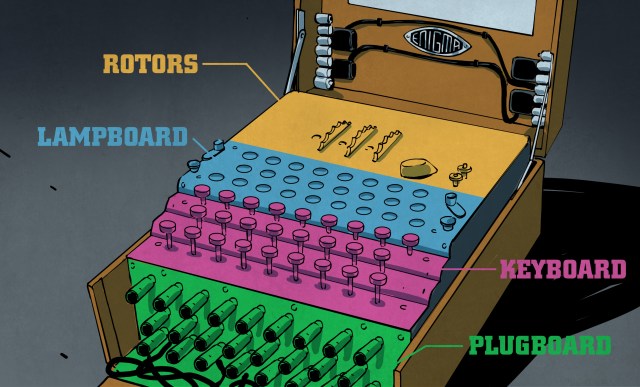



The Enigma Enigma How The Enigma Machine Worked Hackaday




Digitalocean Blog



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf



Exploring The Enigma Plus Maths Org



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf



Q Tbn And9gcrjt7fe0q Rbajjaws1tmrkmopoqgujiemyxudtj4xnlwiqcovd Usqp Cau



Why Did The German Nazis Decide To Design Enigma So That It Wasn T Possible To Map A Plain Text Character To The Same Character In The Cipher Text Quora



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf




Rotor Machine Wikiwand




Exploring The Enigma Plus Maths Org




How Did The Enigma Machine Work Computing The Guardian



Enigma I



No comments:
Post a Comment